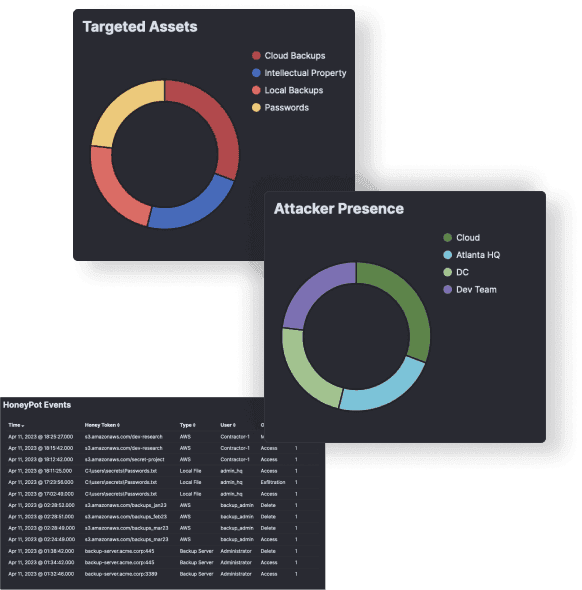
Hacker Deception
Proactively detect and disrupt attackers before they cause harm with Harpy Defence’s advanced Hacker Deception capabilities. By strategically deploying honeypots, honeytokens, and decoy assets across your environment, our deception technology lures threat actors into revealing themselves, allowing your security team to observe their behavior, understand their tactics, and respond before real damage is done.
This proactive defense approach is designed to blend seamlessly with your production environment, creating believable traps that divert attackers away from valuable assets while generating high-fidelity alerts with zero false positives.